
In the article “Operational Risk Management in the Financial Sector”, methodologies and technological innovation trends for managing financial operational risks were discussed. In this article, we will explore the operational Regtech solution offered by Revelis and its related use cases.
Revelis’s approach to operational risk controls
The Regtech solution by Revelis adopts an approach to operational risk monitoring that combines:
- A standardized methodology for data analysis.
- A technological platform integrating a series of functionalities aligned with the technological innovation trends described in the aforementioned article.
Data analysis methodology: CRISP-DM
The delivery of data analysis services and the training of Machine Learning models is carried out using the Cross-Industry Standard Process for Data Mining (CRISP-DM). This is a standard method for the iterative and interactive execution of data mining and analysis processes, structured into three phases and six activities, as illustrated in the following figure.
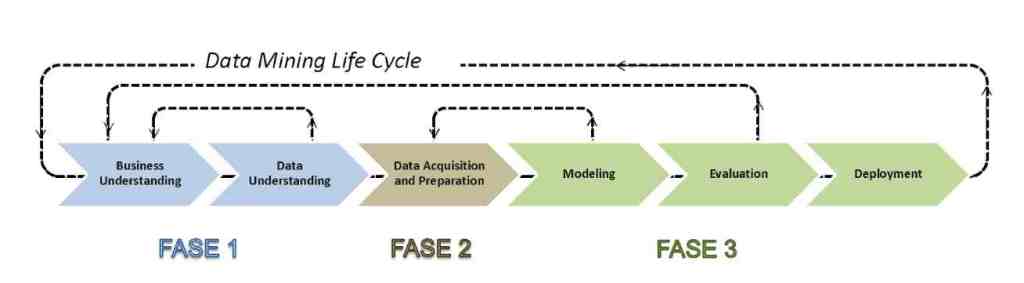
Phase 1
The objective of the preliminary assessment phase is to support the client in estimating, evaluating, and designing the data analysis solution. This phase includes the following activities:
Business Understanding
This step focuses on analyzing the client’s application objectives based on the following tasks:
- Analysis of the “as-is” scenario: Reviewing the current state of the client’s systems and processes.
- Definition of expected results: Establishing the desired outcomes as defined by the client’s decision-makers.
- Definition of evaluation criteria: Setting the standards and metrics used to assess the results of the data analysis process.
Data understanding
This step aims to understand the data and is essential to avoid unforeseen issues during the Data Preparation phase. The tasks performed in this activity include:
- Identification of internal and external data sources: Determining the sources of data relevant to the analysis.
- Identification of significant entities and attributes: Recognizing the key data elements necessary for the analysis.
- Descriptive data analysis: Conducting an initial evaluation of the available data using basic statistical functions, graphs, and aggregations.
- Evaluation of data quality: Identifying potential issues, such as formatting errors or misrepresentation of information.
Phase 2
Phase 2 involves the Data Acquisition and Preparation activity, aimed at connecting to the information sources identified in Phase 1, as well as preparing and cleaning the acquired data. The following tasks are performed during this phase:
- Data Filtering. This task focuses on selecting data relevant to achieving the client’s objectives. It involves “filtering” data and attributes using sampling techniques and/or removing “dirty” data.
- Data Cleaning. Statistical techniques are applied in this task to: Reconstruct missing data, Handle data errors, Fix measurement inaccuracies, Address sparse data issues.
- Creation of Synthetic Data. Raw data is often insufficient to effectively carry out the intended analysis. In such cases, new “plausible” data can be generated from the existing data by employing techniques to derive attributes or generate records.
- Data Integration. Data from different sources referring to the same entities can be integrated through: Merge: Enriching an entity by increasing the number of attributes available. Union: Expanding the number of entities available for analysis.
Phase 3
Phase 3 involves two distinct macro-steps:
1. Formulation and Implementation of the Analysis Model
This step aims to define (using inductive statistical techniques) and evaluate (using standard metrics) one or more data mining models. The activities include:
- Development of Connectors: Connectors are software interfaces that enable the import of data from external systems to be processed by data mining algorithms or the export of results to external systems or platforms.
- Modeling: This involves applying algorithms to an appropriate subset of the available data, called the training set. The training set undergoes preprocessing to ensure it is ready for statistical algorithms. The output is a decision-support model, which can serve various purposes:
- Classification
- Regression
- Segmentation
- Summarization
- Link or association analysis
- Sequence analysis
The algorithms are based on machine learning and deep learning techniques.
- Evaluation:
This activity measures the model’s performance using appropriate metrics from scientific literature. This allows for an objective assessment of the quality of the induced models and verifies whether the defined business objectives are met. Performance evaluation is conducted on a separate subset of the available data, known as the test set, distinct from the training set used during model training.
2. Execution of the Analysis Solution. This step involves the Deployment activity, which is the implementation of an executable version of the induced model. This version can be integrated into the client’s application infrastructure for use.
Technological Framework: The Moneying™ Platform
Moneying™ is the Regtech solution developed by Revelis, consisting of a platform that leverages Artificial Intelligence techniques for data analysis to support operational controls, such as financial transactions and client communications.
The combination of Machine Learning and Deep Learning techniques optimizes verification activities in control processes. The use of Text Analytics techniques enables automated processing of natural language texts, facilitating document management automation for both internal documents and those received from external sources or clients.
Key Features of the Moneying™ Platform, the Moneying™ Regtech solution offers the following key features:
- Scalability:
Moneying™ is a highly scalable platform integrating technologies for Big Data analytics. It can be deployed both on-premises and as-a-service via cloud delivery. - Big Data Analytics:
Moneying™ provides access to over 100 algorithms for data processing and behavior prediction. These algorithms can be combined in various ways to define flexible and highly customizable processing workflows. - Security:
Moneying™ includes a user authentication and profiling system that controls access to data analysis and information, ensuring high-security standards in the client’s operational contexts. - Web Interface:
The analysis of suspicious cases is conducted through a powerful and user-friendly web interface. Users can generate customized reports and access informational dashboards related to the activities performed.
The functional architecture of the Moneying™ platform, the Regtech solution, is illustrated in the following figure.

On the left side (Area 1), the platform represents the range of possible types of information sources that may be relevant to the analysis processes. Specifically, the platform supports:
- Data from internal and external information sources: Data acquisition occurs through dedicated connectors to these sources.
- Various types of data:
- Structured/semi-structured data: Databases, CSV files, XML files.
- Unstructured data: Text documents.
- Process-related data: Logs.
- Multimedia data: Videos, images, audio files.
- Geospatial data.
- Streaming data: From continuous sources or sensors.
- Web and social media data.
- Data types related to customers under analysis:
- Subjective data: Directly linked to the individual being analyzed. This includes demographic information, profession, and residence.
- Objective data: Related to the individual’s operational activities concerning their relationship with the bank. Examples include financial transactions, information on suspicious activity reports, and any other type of alerts.
The listed information sources are subjected to storage and/or analysis processes within the Cloud Infrastructure (Area 2) portion of the architecture. This area is logically divided into two distinct sub-areas:
- Big Data Storage: For data storage.
- AI/Big Data Analytics: For data analysis.
The storage and analysis processes can be implemented entirely separately, either in the cloud or on-premises. Across both sub-areas, various services for security, monitoring, auditing, backup, and disaster recovery are integrated.
The AI/Big Data Analytics section is logically divided into two parts: Core Capabilities and AI Capabilities. The first section includes distributed computing mechanisms, access to file systems (local or distributed), in-memory data access, workload management, and access to both SQL and NoSQL data sources. The second part provides a range of functionalities aligned with the CRISP-DM methodology, supporting the phases of data acquisition, information preparation, model training, and results visualization.
Regarding models, the platform notably offers both Machine Learning and Deep Learning algorithms, as well as mechanisms to enable automated reasoning.
This approach enables the creation of AI solutions that combine knowledge derived from data (sub-symbolic approaches, such as Machine Learning and Deep Learning) with domain expert knowledge (symbolic approaches, such as automated reasoning).
This feature of the platform has two key advantages:
- It allows for the automation of decision-making processes even in cases where available datasets are too small for training Machine/Deep Learning models, as expert logic can be automated through expert systems.
- It addresses challenges associated with sub-symbolic approaches, such as GPT model “hallucinations,” by enabling the implementation of control systems based on automated reasoning to correct such issues.
Finally, on the right side of the figure (Area 3), the application services related to banking controls are represented. A non-exhaustive list of these services includes:
- KYC (Know Your Customer)
- Enhanced Due Diligence
- Account Opening Controls
- Risk Profile Evaluation (credit, default, investment-related risks, etc.)
- AML (Anti-Money Laundering) via Transaction Monitoring
- Monitoring (authorization and spending limits, exposure limits)
- Profiling (creditworthiness, product suitability, etc.)
Completed Use Cases
AML – Transaction Monitoring, Risk Management, Management of Relations with Investigating Authorities
The Moneying™ Regtech solution applies Machine Learning and Reasoning techniques to analyze financial transactions for AML and Risk Management purposes.
Through pattern recognition and profiling techniques, it is possible to identify fraudulent or illegal behavior and enable the assessment of customer risk profiles (KYC).
The platform offers the following functionalities:
- Risk Profile:
Moneying™ enables customer profiling based on a “Risk Profile,” calculated using both objective and subjective customer characteristics. All customer information is integrated to provide a “customer file” containing all relevant details for both B2C and B2B customers. - Anti Money-Laundering:
Moneying™ provides functionalities for processing Big Data related to financial transactions to detect anomalies in the use of financial instruments by one or more individuals. The platform includes a module for generating Suspicious Activity Reports (SARs) to send to the Financial Intelligence Unit (FIU). - Risk Management:
The platform allows for risk evaluation analysis; users can customize data analysis processes to calculate relevant Key Risk Indicators (KRIs). - Monitoring of B2C and B2B Customers:
Moneying™ provides a module to manage the sanctioning of B2C or B2B customers who violate contractual agreements in the use of payment instruments. - Management of Relations with Investigating Authorities:
Moneying™ optimizes interactions with investigating authorities by speeding up the response process to requests from judicial authorities, law enforcement, and courts.
Automatic Analysis of Customer Communications Related to Complaints and Grievances
Currently, in the banking sector, customer support relies on the management of large volumes of emails, which requires a significant amount of time and resources from human operators. By using Artificial Intelligence and Machine Learning techniques, the process of reading and classifying emails can be automated, significantly reducing the workload of operators, eliminating repetitive tasks, and allowing them to focus on other activities, thereby improving overall efficiency.
The “AIOM” vertical of the Moneying™ platform uses Text Intelligence techniques to automatically read and classify emails sent to the Complaints and Legal Departments of a major international bank. This is done by analyzing the content (body of the email and attachments) to direct the processing of complaints and grievances and, when possible, to automatically respond to the customer.
The Benefits of MoneyingAIOM, the Regtech Solution
The use of the MoneyingAIOM platform as a Regtech solution has led to the following impacts:
- Reduction of Operator Workload: The Text Analytics model can automatically handle the reading and classification of emails, significantly reducing the workload of human operators.
- Increased Efficiency: The automatic classification of emails occurs in a fraction of the time compared to manual classification, allowing for faster responses and a smoother workflow.
- Scalability and Flexibility: The automatic email classification system can be easily adapted to handle large volumes of emails without requiring a proportional increase in human resources. Furthermore, the machine learning model can be adjusted and improved over time to meet new needs and changes in email content.
- Cost Savings: By reducing the reliance on human operators for reading and classifying emails, costs associated with managing large volumes of corporate communications have been reduced by 65%.
The implementation of such a system requires special attention to compliance with regulations, such as the General Data Protection Regulation (GDPR) and privacy protection laws. Emails contain personal or confidential information that must be safeguarded. Once read by the MoneyingAIOM platform, the email texts, attachments examined, and sender information are stored in an encrypted manner.
Enhanced Due Diligence (EDD)
Enhanced Due Diligence (EDD) is a process aimed at mitigating the risk of money laundering and terrorist financing. The manual execution of the EDD process involves the following stages:
- Information Acquisition: Operators manually connect to various internal and external systems to acquire the necessary information for analysis, such as:
- Verification of the existence of the tax code and VAT number (information publicly available on the Revenue Agency’s website);
- A list of completed transactions;
- The risk profile of the subject;
- Whether the subject is on PEP (Politically Exposed Persons) or anti-terrorism lists.
- Risk Analysis and Assessment: Operators review the acquired information to identify any risk factors and proceed with the overall risk assessment of the client, considering:
- The intrinsic risk profile (activities performed, PEP status, involved countries);
- The client’s behavior (suspicious transactions, consistency with provided information);
- The risk level associated with the monitored product or service.
- Enhanced Verification Measures: For high-risk subjects, a questionnaire is prepared, requesting the subject to justify a series of transactions and potentially provide additional documentation (e.g., company records, bank statements). In this phase, it may also be possible to request information from third-party sources (e.g., databases, competent authorities).
- Updating and Monitoring: Operators send the questionnaires and monitor the response from the analyzed subject. In case of no response, the closure of the existing relationships may be proposed.
The manual execution of EDD requires:
- Qualified Personnel: Employees trained on anti-money laundering procedures and capable of assessing risk.
- Defined Internal Procedures: Detailed documentation of EDD procedures and risk assessment criteria.
- Supervision and Control: A supervisory system to ensure the proper application of procedures.
The automation of EDD operations is performed through an IT system, whose functional architecture is shown in the following figure.

In particular, through appropriate RPA procedures, it is possible to acquire all the information necessary for analysis, which consists of a series of PDF or Excel files that are stored in a dedicated folder.
Using this data, the platform will utilize the Moneying™ platform by Revelis to:
- Automatically extract information from the files, taking into account the type (PDF, CSV, etc.) and structure of the files;
- Implement the decision-making logic related to EDD, starting from a series of “Golden rules” defined by the operators and represented using appropriate formalism in Answer Set Programming.
The process executed through Moneying™ produces, for each position to be analyzed, an outcome indicating whether the subject should or should not be subjected to the EDD questionnaire, and, in some cases, the structure of the questionnaire to be administered.
Other possible applications of AI in the field of controls to safeguard operational risks.
Automating KYC with Artificial Intelligence
Artificial Intelligence (AI) offers tremendous potential to automate the Know Your Customer (KYC) process in the banking and financial sector. Below are some applications that use AI techniques to improve the efficiency and effectiveness of these procedures:
- Facial Recognition and Biometrics. Using computer vision techniques, it is possible to analyze customers’ faces and fingerprints to verify their identity in real-time, using a streaming video. This eliminates the need for paper documents and allows for remote verification.
- Natural Language Processing (NLP) Analysis. As already analyzed in the context of customer communication analysis and AVR, Text Analytics techniques can be used to analyze information provided by customers in KYC and AML forms to identify potential risks. Specifically, the use of Natural Language Processing allows for extracting data from documents such as invoices and bank transfers to identify any suspicious transactions.
Automating Account Opening Requirement Checks with AI
Artificial Intelligence (AI) can be used to automate account opening requirement checks in several ways:
- Risk Analysis. Expert systems (symbolic approaches) can be used to apply evaluation rules to the information provided by customers in account opening request forms, identifying potential risks. Symbolic approaches can be combined with sub-symbolic approaches related to Machine Learning and Neural Networks to profile customers based on the risk of fraud, terrorism financing, and other financial risks.
- Identity Verification. As previously described in the KYC case, AI can be used to verify customers’ identities through facial recognition, document analysis, and biometric verification, preventing fraud and identity theft.
- Background Checks. AI can be used to check customers’ backgrounds to identify any criminal records or financial sanctions. This helps protect the bank from reputational and legal risks.
Author: Francesco Cupello
